 For much of the last decade, innovation in video surveillance has been driven by visible capabilities—higher resolution, smarter analytics, faster alerts, and AI at the edge. These advancements have transformed cameras from passive recording devices into intelligent systems capable of real-time decision-making.
For much of the last decade, innovation in video surveillance has been driven by visible capabilities—higher resolution, smarter analytics, faster alerts, and AI at the edge. These advancements have transformed cameras from passive recording devices into intelligent systems capable of real-time decision-making.
But as we move into 2026, a new question is beginning to dominate serious conversations around surveillance deployments:
Can these intelligent systems be trusted?
As cameras become autonomous, connected, and deeply embedded into critical infrastructure, trust is no longer an abstract concept. It is becoming a fundamental requirement.
The Expanding Role of the Camera
- Modern surveillance cameras are no longer isolated endpoints. They are now:
- Networked computing devices
- AI-powered edge processors
- Part of enterprise IT and OT ecosystems
- Remotely managed and frequently updated
- Integrated with access control, alarms, and operational systems
In effect, cameras have become edge computers with vision.
This evolution brings enormous value—but it also expands the attack surface. A compromised camera is no longer just a blind spot; it can become an entry point, a data risk, or a system-wide vulnerability.
Why Software Security Alone Is Not Enough
Historically, cybersecurity in surveillance has focused on software:
- Password policies
- Network hardening
- Encrypted communication
- Secure firmware updates
While these measures are necessary, they are no longer sufficient.
- Software can be altered.
- Firmware can be replaced.
- Credentials can be stolen.
True security must begin below the operating system, at the hardware level.
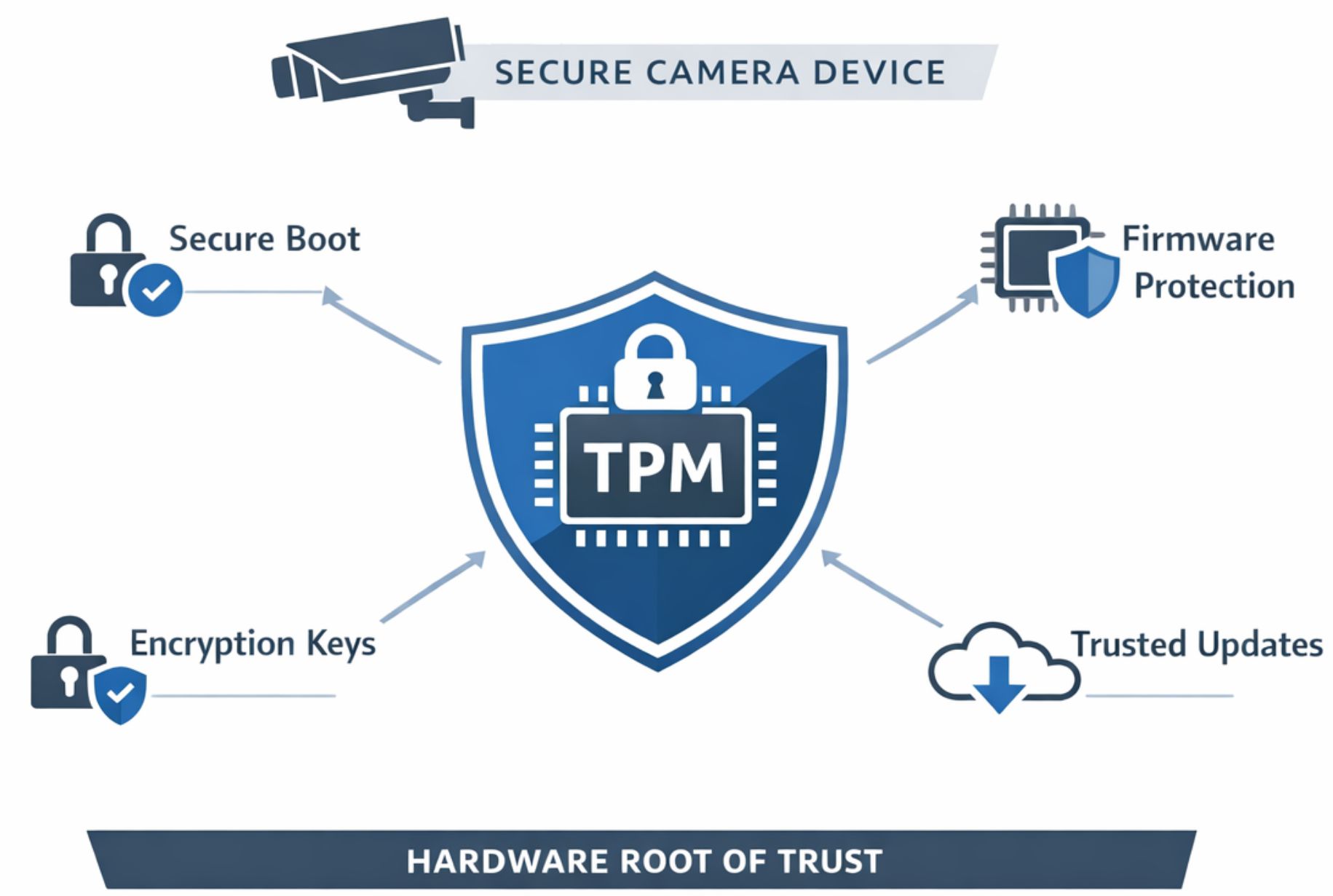
This is where Trusted Platform Module (TPM) technology becomes critical.
TPM: The Silent Foundation of Trust
TPM is not a feature users interact with, and it does not appear on dashboards or analytics reports. Yet it plays one of the most important roles in next-generation surveillance architecture.
At its core, TPM provides a hardware root of trust-a secure, tamper-resistant foundation that ensures a device starts, operates, and updates only in a verified and trusted state.
In simple terms, TPM ensures that:
- The camera boots only with authentic firmware
- Unauthorized code cannot run silently in the background
- Cryptographic keys are protected in hardware, not software
- Device identity cannot be cloned or spoofed
- Updates and configurations remain secure over the lifecycle
This trust is not assumed-it is mathematically and physically enforced.
Why Trust Is Becoming Mission-Critical
As surveillance systems expand across cities, transportation networks, utilities, and industrial facilities, expectations are changing.
Organizations now demand:
- Long device lifecycles
- Secure remote management
- Protection against supply-chain risks
- Confidence in firmware authenticity
- Compliance with national and sector-specific cybersecurity norms
In such environments, a camera that performs well but cannot be trusted is a liability.
TPM addresses this challenge by ensuring that intelligence, connectivity, and autonomy operate within a secure and verifiable framework.
Edge Intelligence Needs a Trusted Core
Edge AI is reshaping surveillance by enabling cameras to detect, classify, and respond locally. However, intelligence without trust introduces new risks.
If an edge device is compromised:
- Analytics results can be manipulated
- Alerts can be suppressed or falsely generated
- Video streams can be intercepted
- The device itself can be weaponized
TPM ensures that edge intelligence operates inside a trusted envelope, preserving the integrity of decisions made at the device level.
This is especially important as cameras begin to take autonomous actions—triggering alarms, controlling PTZ movements, or integrating with safety and operational systems.
Trust Beyond Cybersecurity: Operational Confidence
Hardware-rooted security is not only about protection from cyber threats. It also contributes to operational reliability and confidence.
In large deployments, TPM enables:
- Secure commissioning and provisioning
- Confident remote updates without fear of corruption
- Faster fault isolation
- Reduced risk during long-term operation
- Stronger compliance posture for audits and tenders
For organizations operating in regulated or high-risk environments, this confidence is becoming a decisive factor in technology selection.
 As cameras evolve into intelligent edge devices, they also become part of an organization’s digital trust framework. AI without integrity is a risk. Hardware-rooted security, such as TPM, ensures that intelligence operates on a foundation of trust, resilience, and long-term reliability.”
As cameras evolve into intelligent edge devices, they also become part of an organization’s digital trust framework. AI without integrity is a risk. Hardware-rooted security, such as TPM, ensures that intelligence operates on a foundation of trust, resilience, and long-term reliability.”
— Gaurav Taywade, Managing Director – India, Vicon
The Direction of Next-Generation Surveillance
Looking ahead, the most advanced surveillance platforms will be defined by a combination of:
- Edge intelligence
- Rugged, purpose-built hardware
- Secure lifecycle management
- Hardware-enforced trust
TPM is becoming a silent prerequisite for this evolution-often unnoticed, but absolutely essential.
As intelligent sensors become more autonomous and more deeply integrated into critical operations, trust will no longer be optional or assumed. It will be designed into the device from day one.
Conclusion
The video surveillance industry is entering a new phase-one where intelligence, autonomy, and connectivity must be balanced with integrity and trust.
While AI and analytics will continue to drive visible innovation, hardware-rooted security will quietly determine which platforms are truly ready for the future.
In the coming years, the most valuable cameras will not only be the smartest—but the most trusted.
https://vicon-security.com/india























































