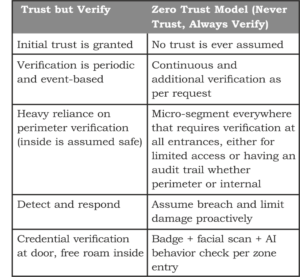
 ‘Zero Trust’ was a new security model that revolutionized the cybersecurity space. Zero Trust stems from challenging popular belief at the time which was ‘Trust but verify’. It is a no-brainer to extend this concept to Physical Security. Extending the cybersecurity “never trust, always verify” model to physical spaces requires continuous authentication, authorization, and validation for all access regardless of location or prior permissions.
‘Zero Trust’ was a new security model that revolutionized the cybersecurity space. Zero Trust stems from challenging popular belief at the time which was ‘Trust but verify’. It is a no-brainer to extend this concept to Physical Security. Extending the cybersecurity “never trust, always verify” model to physical spaces requires continuous authentication, authorization, and validation for all access regardless of location or prior permissions.
Zero Trust originated in IT to combat perimeter-based defense failures by assuming breaches are inevitable. In physical security, it applies the same concept to facilities for constant vetting via identity, device, behavior, and context checks. This counters the rising hybrid threats where IoT, surveillance and access systems integrate with networks.
 Why It Matters Now
Why It Matters Now
Traditional physical security relies on physical keys or fences for perimeter access but grant broad trust within premises. This leaves facilities vulnerable to insiders, tailgating or stolen credentials. With remote work, multi-site access needs and advancing threats, Zero Trust protects data centers, offices, airports, warehouses and more by treating every entry as risky.
Core Principles
- Explicit Verification: Every access request demands rigorous identity proof using multi-factor authentication (MFA), combining biometrics, possession (badges, mobile credentials, RFIDs) and knowledge (PINs, passwords). Unlike single credentials vulnerable to theft, these layered checks via systems create multilayered verification for every entry and continuously re-verify post-access flags like unusual device pairing.
- Least Privilege: Access is tightly scoped to a user’s role, current time, location and risk level, enforced dynamically via role-based access control (RBAC). An employee might enter the lobby anytime but needs extra approval for server rooms after hours; privileges auto-revoke on job changes or anomalies. This minimizes damage from compromised insiders, using policy engines to grant just-in-time access.
- Assume Breach: Treat every environment as compromised, mandating 24/7 monitoring with cameras, sensors, door logs and behavior patterns. Real-time anomaly detection like tailgating should trigger alerts or escalations to make human vigilance more reliable and feasible.
- Micro-Segmentation: Facilities are divided into granular zones or departments (e.g., public lobby vs. high-security data vaults) with escalating controls like barriers, smart and electrified locks and sensors at each boundary. This means breaches in one area can’t spread laterally, as crossing zones requires another breach of verification. In practice, server rooms might demand 3FA plus geofencing, while offices use 2FA.
How ASSA ABLOY Implements The Zero Trust Model
Zero Trust operates via a policy engine evaluating requests against real-time data: user identity, device health (OS patches, apps), geolocation, behavior patterns, and threat intel. Access is granted per-session, not perpetually. For example, an employee badge alone fails; it needs facial scan plus normal hours confirmation. AI flags oddities like off-hours entry, triggering alerts or lockdowns.
Step 1: Assess Vulnerabilities
Implementation steps for Zero Trust Physical Security start with mapping assets to identify the gaps and requirements for the level of security. ASSA ABLOY does this with our specification consultants who look at the project in BIM software visualize and create detailed reports and schedules suggesting the appropriate balance between convenience, safety, security and sustainability.
Step 2: Map Access Points and Flows and Identify Weak Spots
These specification services allows cataloging every door, turnstile, elevator, sensor, camera and user paths. Assessing and mapping user circulation helps reveal blind spots like service entrances or rooftop vents, unmonitored back doors, tailgate-prone lobbies, legacy locks without logs. Digital twins or BIM software predict and show clashes to proactively take care of any issues that might crop up later. This way projects can preemptively prioritize fixes based on risk: high-value assets like server rooms first.
Step 4: Deploy Tech Layers
 Control iD biometrics, ASSA ABLOY Aperio locks, CLIQ with RBAC, and Primo platforms enable robust Zero Trust Physical Security through secure, scalable, integrated tech tailored for MFA and monitoring.
Control iD biometrics, ASSA ABLOY Aperio locks, CLIQ with RBAC, and Primo platforms enable robust Zero Trust Physical Security through secure, scalable, integrated tech tailored for MFA and monitoring.
- Control iD Biometrics/Facial Recognition: Control iD iDAccess systems feature 500 DPI optical fingerprint readers storing up to 100,000 prints in online mode, integrating seamlessly with MIFARE/125kHz cards, PINs, and passwords for MFA. Fingerprints impossible to duplicate, they support 200,000+ users, cloud sync for backups and restrictions by group/schedule; compact for entry points is what makes Ideal for high-traffic facilities.
 ASSA ABLOY Aperio Smart Locks & Handles: Aperio wireless locks retrofit existing doors without wiring, using RFID cards or mobile creds for real-time monitoring, tamper alerts, and audit trails (up to 1,000 cached creds, 10 overrides). Grade 1 mechanics handle -40°C to +65°C, with LEDs/sensors for bolt/door status; integrates via hubs/RS485 for EAC systems, scalable to thousands of doors.
ASSA ABLOY Aperio Smart Locks & Handles: Aperio wireless locks retrofit existing doors without wiring, using RFID cards or mobile creds for real-time monitoring, tamper alerts, and audit trails (up to 1,000 cached creds, 10 overrides). Grade 1 mechanics handle -40°C to +65°C, with LEDs/sensors for bolt/door status; integrates via hubs/RS485 for EAC systems, scalable to thousands of doors.
Fire/escape compliant, reducing key risks.
- RBAC with CLIQ: ASSA ABLOY CLIQ (e.g., PROTEC² CLIQ) blends mechanical high-security keys with electronic management via CLIQ Web/Local Manager for RBAC: program keys per user/need like the site, schedule, department and role, revoke lost ones remotely without rekeying. Audit trails track access; browser/SaaS options enable dynamic privileges for real-time updates across 100+ sites.
Suited for utilities/high-risk areas.
Step 5: Staff Communication, Maintenance and Auditing
Routine checks as breach protection, automated audit trails via dashboards logging all events, set alerts for failures, regular drills, policy and firmware updates ensure compliance, reduce resistance and make sure to prevent problems rather than having to solve them and then mitigate damage. Phased rollout starting from high-risk zones maximize ROI for facilities with scalable solution options.
Benefits
 Enhanced Protection: Continuous verification blocks unauthorized entries, reducing insider threats, damage to life or property and lateral movement e.g., a compromised biometric scanner can be contained via micro-segmentation in a bank case, preventing wider damage. AI monitoring spots anomalies like off-hours access instantly.
Enhanced Protection: Continuous verification blocks unauthorized entries, reducing insider threats, damage to life or property and lateral movement e.g., a compromised biometric scanner can be contained via micro-segmentation in a bank case, preventing wider damage. AI monitoring spots anomalies like off-hours access instantly.
- Reduced Risks and Costs: Least privilege minimizes immediate as well as long term damage via efficient threat containment. No more broad insider access cuts negligence risks.
- Compliance and Visibility: Audit trails and real-time logs meet GDPR/HIPAA/NIST; unified platforms provide full traffic/user behavior views for audits and adjustments.
- Operational Benefits: Supports hybrid work with seamless MFA/SSO; faster incident response via automation. Scalable for remote sites, boosting productivity without security trade-offs.
Challenges and Solutions
Adoption hurdles including legacy systems integration are the prominent present challenge. The way ASSA ABLOY approaches this problem is by making our solutions compatible with a phased rollout. Starting only with high-risk areas with ABLOY Locks and frictionless biometrics of iD Face, ASSA ABLOY offers scalable solutions with Aperio and Primo software making it a smart solution budget-wise, integration-wise, tracking wise and metrics about unauthorized attempts blocked or response times.























































